EDC17C54 — VW Amarok 2.0 TDI: Reverse Engineering & Multimap (Playlist)
⚙️ EDC17C54 “VW Amarok 2.0 TDI” — Reverse Engineering & Multimap
This series shows the practical, end-to-end workflow I use to engineer a switchable multimap on Bosch EDC17C54 (TriCore) for the Amarok: bench read, signal discovery on CAN, RAM observation via UDS, and tight hooks written with Ghidra’s help. It’s aimed at practitioners who want the why behind each step, not just files.
1) Bench read & workspace¶
- Full ECU read (bench/boot) to get code + data segments for static analysis.
- Build a memory map (flash, overlay segments, RAM) and note TriCore address windows.
- Baseline checksums + stock behavior logs to compare later.
Goal: a reproducible workspace that pairs binary truth with runtime truth.
2) Finding ECU entry points (CAN)¶
- Quick SocketCAN sweep to capture driver inputs (e.g., cruise/resume/cancel, pedal, mode bits).
- Tag candidate signals → correlate with ROM code paths that consume them.
- Keep a small signal dictionary (ID, start bit, length, scale) you can reuse when iterating maps.
3) Static reversing with Ghidra (TriCore)¶
- Identify OS tasks, comms stack, ADC → torque path, and map lookup helpers (2D/3D, axis transforms).
- Name hotspots: Driver Wish, torque limiters, smoke/rail/boost constraints, torque-to-IQ.
- Place test hooks as tiny stubs so you can toggle logic without destabilizing factory tasks.
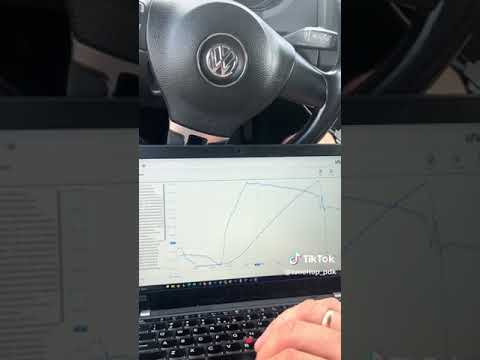
4) Live RAM via UDS (watch, don’t guess)¶
Watching RAM removes guesswork: confirm mode bits, map index, limiter hits, and blending behavior.
# demo-only: UDS 0x23 to watch a RAM byte (e.g., map index / mode flag)
# Requires a proper UDS client + transport (ISOTP) on SocketCAN.
from uds import UDSClient
ADDR, LEN = 0x00ABCDEF, 1 # resolved from RAM sweep
with UDSClient(channel="can0", req_id=0x7E0, res_id=0x7E8) as c:
raw = c.read_memory_by_address(addr=ADDR, length=LEN)
print("Map index:", int.from_bytes(raw, "big"))
5) Multimap design (clean and safe)¶
- Index variable in RAM → used by a thin dispatcher that selects calibrated tables.
- Inputs: a harmless CAN-derived state (e.g., cruise buttons) or a service flag.
- Safety: default to stock, guard against invalid indices, keep checksums stable, and never block OEM diagnostics.
6) Results & testing¶
- Compare logs: pedal → requested torque → limiters → resulting IQ/boost.
- Validate repeatability (hot/cold, idle/load transitions) and watchdog friendliness.
- Keep per-map notes (intended use, deltas vs. stock, constraints hit).
7) What you can analyze from these videos¶
- How to bridge static reversing (Ghidra) with live verification (UDS + CAN sniffing).
- Recognizing Bosch map access patterns and axis math on TriCore.
- Building non-intrusive hooks that survive resets and diagnostics.
- Designing switchable maps you can port to other EDC17 variants (C54/C64/etc.).
- Practical UDS usage: ReadMemoryByAddress (0x23) to validate RAM variables for mode/index.
- Safe rollout mindset: watchdog friendliness, diagnostics compatibility, and checksum hygiene.
📺 Watch the videos (playlist + individual)¶
Full playlist:
https://www.youtube.com/watch?v=gYXH4dHSvl4&list=PLa45wyF5YH7YLDryXHwJYGz58Mj0GFOHl
1) Preview — VW EDC17 Reverse Engineering Multimap Project¶
2) Deep-dive — VW EDC17: Ghidra, CAN Bus Sniffing, and Signal Reversing¶
3) On-ECU testing — VW EDC17: Ghidra Multimap Testing & New Program in ECU¶
4) Results — VW EDC17 Reverse Engineering: Multimap Results & Testing¶
#vw#amarok#edc17c54#bosch#tricore#reverse-engineering#ghidra#can#uds#isotp#multimap